IT SERVICES
Managed Services
We can manage, maintain, troubleshoot, monitor and support your entire IT infrastructure for one monthly not rate. Our Managed Services offering provides gained efficiencies, lower risks and allows you to maintain control while managing your costs better.
We can offer a proactive managed service package that will get your IT environment fixed, fast, stabilized and secured, so we’re able to solve problems when they’re still just warning signs — all for a flat, all inclusive monthly fee.
Our Managed Services Include:
- 24/7 Network Monitoring
- Antivirus and Patch Management
- Preventative Maintenance
- Onsite and Remote Support with 1 Hour Emergency Response
- Hourly Image Based Backups and Loaner Equipment
- Quarterly Roadmap Meetings
- Hardware and Software Purchasing
- Mobile Device Support
- Flat Rate Guaranteed Hassle Free Billing
- Discounted Programming and Project Work
Cyber Security
DBP can provide a strong security foundation with interconnected solutions that span the enterprise, keeping in mind the following trends that affect the cyber security:
First, the Internet will become a fundamental element of our business mindset. Second, flexible working practices facilitated by mobility will become a basic lifestyle option, with borderless enterprises becoming an essential form of business operations. Third, through effective use of the Internet, cloud computing, and big data, mankind can leverage the wisdom of people and machines worldwide to create a new, connected and shared wisdom.Finally, as the Internet and social media continue to gain popularity, the behaviors and preferences of consumers and individuals are converging, and intelligent analytics can be harnessed for business benefits. As the boundary between niche and domestic markets is increasingly vague as a result, enterprises must evolve to do business globally.
Our Cyber Security services have the following basic phases:
Understand Cyber Security Requirements
The purpose of this first phase is to understand the program’s Cyber Security requirements and to develop an initial approach and plan for conducting Cyber Security test and evaluation. In collaborating all departments/group in an Organization, we will examine all available program documents to gain an understanding of system Cyber Security requirements.
Characterize the Cyber-Attack Surface
In this phase, the opportunities an attacker may use to exploit the system are identified in order to plan testing that evaluates whether those opportunities continue to allow exploitation. The cyber-attack surface will be characterized in conjunction with the systems security engineering process.
Cooperative Vulnerability Identification
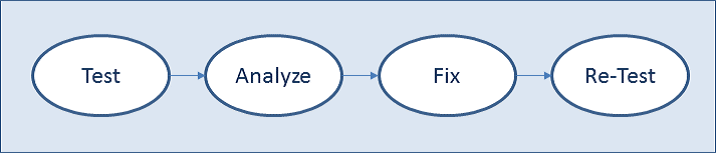
This phase includes detailed test planning and execution of vulnerability testing. This testing and analysis is performed to support and provide feedback to the Critical Design Review (CDR) and as input to and in preparation for the Test Readiness Review (TRR). Note that vulnerability testing may consist of one or more test events. The purpose of this phase is to identify vulnerabilities that may be fed back to systems designers, developers, and engineers so that mitigations can be implemented to improve resilience. This test, analyze, fix, re-test process, shown in Figure below, provides the early and ongoing feedback, addressing Cyber Security vulnerabilities throughout system development so that mitigations can be cost effectively implemented early in the system deployment lifecycle.
Adversarial Cyber Security
This phase includes an evaluation of the system’s Cyber Security in a mission context, using realistic threat exploitation techniques, while in a representative operating environment.
Cooperative Vulnerability and Penetration Assessment
The purpose of this phase is to provide a comprehensive characterization of the Cyber Security status of a system in a fully operational context, and to substitute for reconnaissance activities in support of adversarial testing when necessary. This phase consists of an overt and cooperative examination of the system to identify vulnerabilities.
Adversarial Assessment
This phase assesses the ability of a unit equipped with a system to support its missions while withstanding validated and representative cyber threat activity. In addition to assessing the effect on mission execution, we will evaluate the ability to protect the system, detect threat activity, react to threat activity, and restore mission capability degraded or lost due to threat activity. It includes adversarial assessment testing, which emulates the threats described in the program’s validated threat capabilities document.
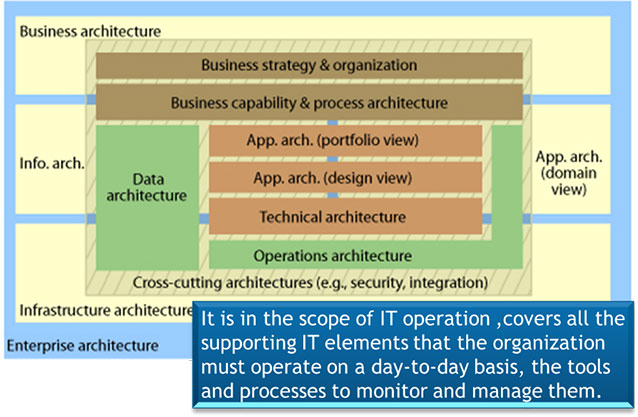
Enterprise IT & Architecture Solutions (Software & System Development and Deployment)
DBP can support the entire enterprise to solve, maintain and modernize its IT infrastructure and architecture environment keeping in mind the demands of cloud services, software solutions, Software Defined Network (SDN) requirements, Internet of Things (IoT) demands, globalized and social media based workforce and market places. In this area, we would adhere to the principles of CMMI, ITIL, etc. Whether it’s for, cloud implementation, virtualization, SOA requirements, or social media based, our software & system development services are foundationally based on an Enterprise Architecture based strategy, as explained below:
Through our Enterprise Architecture services, we help our customers:
- To manage the IT change and the individuals and teams involved
- To tailor the transformation using a formal but adaptive process that is based on your unique starting point of staff skills, project mix, business priorities and challenges
- To align the technology planning with business strategy
The Components of Enterprise Architecture services we can provide are:
- Business Architecture : The function of the business architecture is to clarify, elaborate, and illuminate the business model (how an organization creates value) to create new insight and perspective, identify opportunities, and provide a foundation for creating a cohesive business operating model. providing a business-focused design foundation for an ongoing stream of business technology solution delivery.
- Data Architecture (Info Architecture ) : Most strategically, data architecture defines data and data relationships (structured and unstructured) to facilitate analyses that feed business strategy and optimization decisions (e.g. through data warehousing and BI applications).
- Application architecture : It begins with the identification of the applications needed to support the business and carries through to the design and construction (or acquisition) as well as the integration of applications. This will also include software systems development and deployment to meet customers’ business requirements.
Infrastructure architecture and whole structure